A software engineer needs to transfer data over the internet using programmatic access while also being able to query the data. Which of the following will best help the engineer to complete this task?
CV0-004 Free Sample Questions
Comptia Cloud+ Practice TestWhich of the following is a field of computer science that enables computers to identify and understand objects and people in images and videos?
A company needs to deploy its own code directly in the cloud without provisioning additional infrastructure. Which of the following is the best cloud service model for the company to use?
A company just learned that the data in its object storage was accessed by an unauthorized party. Which of the following should the company have done to make the data unusable? A.The company should have switched from object storage to file storage.B.The company should have hashed the data.C.The company should have changed the file access permissions.D.The company should have encrypted the data at rest.
A customer relationship management application, which is hosted in a public cloud IaaS network, is vulnerable to a remote command execution vulnerability. Which of the following is the best solution for the security engineer to implement to prevent the application from being exploited by basic attacks?
Which of the following is a difference between a SAN and a NAS?
A cloud engineer is troubleshooting an application that consumes multiple third-party REST APIs. The application is randomly experiencing high latency. Which of the following would best help determine the source of the latency?
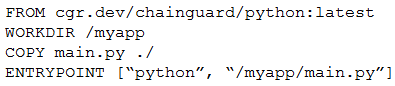
A cloud engineer is reviewing the following Dockerfile to deploy a Python web application:Which of the following changes should the engineer make to the file to improve container security? A.Add the instruction USER nonroot.B.Change the version from latest to 3.11.C.Remove the ENTRYPOINT instruction.D.Ensure myapp/main/py is owned by root.
A financial services company is deploying a new containerized application to an Amazon EKS cluster. A recent security audit mandates that all container images must be scanned for vulnerabilities before being admitted to the cluster, and deployments with 'CRITICAL' severity vulnerabilities must be blocked. Which combination of tools and configurations BEST enforces this policy in an automated fashion?
A lead SRE is designing a monitoring strategy for a distributed application that spans multiple geographic regions and cloud providers. The primary goal is to gain deep insights into request flows and pinpoint performance bottlenecks across service boundaries. Which observability practice is MOST critical to achieving this goal?