Which of the following is the feature that separates the use of Rainbow Tables from other applications such as Cain or John the Ripper?
GPEN Free Sample Questions
GIAC Penetration Tester Practice TestWhen attempting to crack a password using Rainbow Tables, what is the output of the reduction function?
What will the following soapy commands do?

John works as a professional Ethical Hacker. He has been assigned the project of testing the security of www.we-are-secure.com. He has successfully performed the following steps of the preattack phase to check the security of the We-are-secure network: I Gathering information I Determining the network range I Identifying active systems Now, he wants to find the open ports and applications running on the network. Which of the following tools will he use to accomplish his task?
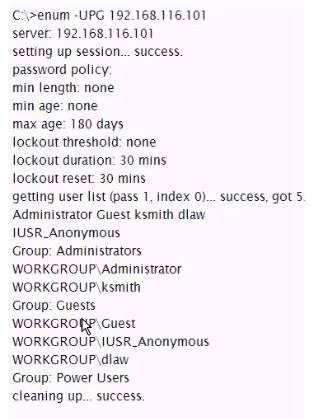
Analyze the command output below, what action is being performed by the tester?
Which Metasploitvncinject stager will allow VNC communications from the attacker to a listening port of the attacker's choosing on the victim machine?
Analyze the output of the two commands below: Which of the following can be factually inferred from the results of these commands?
What difference would you expect to result from running the following commands; (I). S dig ©ns domain.com target.com -t AXFR and (2). S dig ©ns.domain.comtarget.com -t IXFR=1002200301
LM hash is one of the password schemes that Microsoft LAN Manager and Microsoft Windows versions prior to the Windows Vista use to store user passwords that are less than 15 characters long. If you provide a password seven characters or less, the second half of the LM hash is always _______.
You successfully compromise a target system's web application using blind command injection. The command you injected is ping-n 1 192.168.1.200. Assuming your machine is 192.168.1 200, which of the following would you see?