What must you do first to use the Monitor/Alarms/Policy Log workspace in J-Web?
JN0-230 Free Sample Questions
Security, Associate Practice TestWhat is a type of security feed that Sky ATP provides to a vSRX Series device by default?
You configured and applied several global policies and some of the policies have overlapping match criteria. In this scenario, how are these global policies applied?
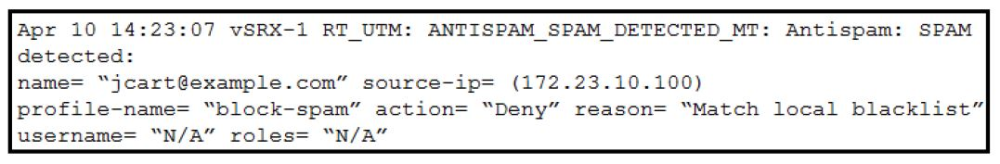
Click the Exhibit button. You have configured antispam to allow e-mails from example.com; however, reviewing the logs you see [email protected] is blocked. Referring to the exhibit, what are two ways to solve this problem? (Choose two.)
Which two statements are correct about global security policies? (Choose two.)
You have created a zone-based security policy that permits traffic to a specific webserver for the marketing team. Other groups in the company are not permitted to access the webserver. When marketing users attempt to access the server they are unable to do so. What are two reasons for this access failure? (Choose two.)