A company’s Chief Operating Officer (COO) is concerned about the potential for competitors to infer proprietary information gathered from employees’ social media accounts. Which of the following methods should the company use to gauge its own social media threat level without targeting individual employees?
CAS-003 Free Sample Questions
CompTIA Advanced Security Practitioner (CASP) Practice TestA security administrator is hardening a TrustedSolaris server that processes sensitive data. The data owner has established the following security requirements: The data is for internal consumption only and shall not be distributed to outside individuals The systems administrator should not have access to the data processed by the server The integrity of the kernel image is maintained Which of the following host-based security controls BEST enforce the data owner’s requirements? (Choose three.)
An SQL database is no longer accessible online due to a recent security breach. An investigation reveals that unauthorized access to the database was possible due to an SQL injection vulnerability. To prevent this type of breach in the future, which of the following security controls should be put in place before bringing the database back online? (Choose two.)
A company has entered into a business agreement with a business partner for managed human resources services. The Chief Information Security Officer (CISO) has been asked to provide documentation that is required to set up a business-to-business VPN between the two organizations. Which of the following is required in this scenario?
Given the output blow from a local PC. Which of the following ACLs on a stateful host-based firewall would allow the PC to serve an intranet website?
A penetration tester has been contracted to conduct a physical assessment of a site. Which of the following is the MOST plausible method of social engineering to be conducted during this engagement?
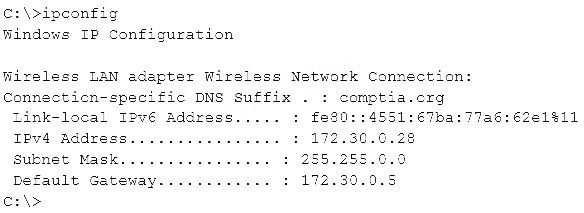
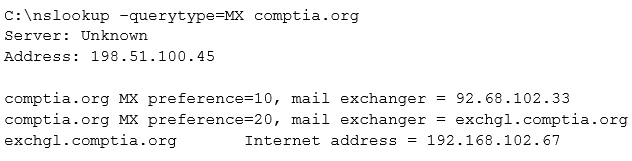
A penetration tester is conducting an assessment on Comptia.org and runs the command below from a coffee shop while connected to the public Internet. Which of the following should the penetration tester conclude about the command output?
Two new technical SMB security settings have been enforced and have also become policies that increase secure communications. Network Client: Digitally sign communication Network Server: Digitally sign communication A storage administrator in a remote location with a legacy storage array, which contains timesensitive data, reports employees can no longer connect to their department shares. Which of the following mitigation strategies should an information security manager recommend to the data owner?