During a web application assessment, a penetration tester discovers that arbitrary commands can be executed on the server. Wanting to take this attack one step further, the penetration tester begins to explore ways to gain a reverse shell backto the attacking machine at 192.168.1.5. Which ofthefollowing are possible ways to do so? (Select TWO).
PT0-001 Free Sample Questions
PenTest+ Practice TestA penetration tester has been assigned to perform an external penetration assessment ofa company. Which ofthe following steps would BEST help with the passive-information-gathering process? (Choose two.)
A penetration tester has been asked to conduct a penetration test on a REST-based web service. Which ofthe following items is required?
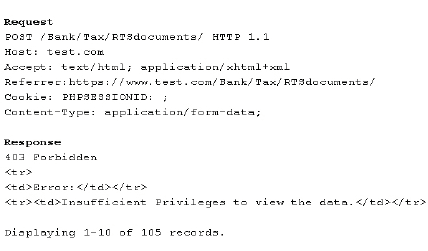
A penetration tester is testing a banking application and uncovers a vulnerability. The tester is logged in as a non-privileged user who should have no access to any data. Given the data below from the web interception proxy: Which ofthe following types ofvulnerabilities is being exploited?
A penetration tester has a full shell to a domain controller and wants to discover any user account that has not authenticated to the domain in 21 days. Which ofthe following commands would BEST accomplish this?
A penetration tester has compromised a Windows server and is attempting to achieve persistence. Which ofthe following would achieve that goal?