When should an MD5 hash check be performed when processing evidence?
EC0-349 Free Sample Questions
Computer Hacking Forensic Investigator Practice TestYou are running through a series oftests on your network to check for any security vulnerabilities. After normal working hours, you initiate a DoS attack against your external firewall. The firewall Quickly freezes up and becomes unusable. You then initiate an FTP connection from an external IP into your internal network. The connection is successful even though you have FTP blocked at the external firewall. What has happened?
Which of the following is NOT a graphics file?
Michael works for Kimball Construction Company as senior security analyst. As part ofyearly security audit, Michael scans his network for vulnerabilities. Using Nmap, Michael conducts XMAS scan and most of the ports scanned do not give a response. In what state are these ports?
What is a good security method to prevent unauthorized users from 'tailgating'?
What technique is used by JPEGs for compression?
Which is a standard procedure to perform during all computer forensics investigations?
Your company uses Cisco routers exclusively throughout the network. After securing the routers to the best of your knowledge, an outside security firm is brought in to assess the network security. Although they found very few issues, they were able to enumerate the model, OS version, and capabilities for all your Cisco routers with very little effort. Which feature will you disable to eliminate the ability to enumerate this information on your Cisco routers?
The police believe that Mevin Matthew has been obtaining unauthorized access to computers belonging to numerous computer software and computer operating systems manufacturers, cellular telephone manufacturers, Internet Service Providers, and educational institutions. They also suspectthat he has been stealing, copying, and misappropriating proprietary computer software belonging to the several victim companies. What is preventing the police from breaking down the suspect door and searching his home and seizing all of his computer equipment ifthey haveis preventing the police from breaking down the suspect? door and searching his home and seizing all of his computer equipment ifthey have not yet obtained a warrant?
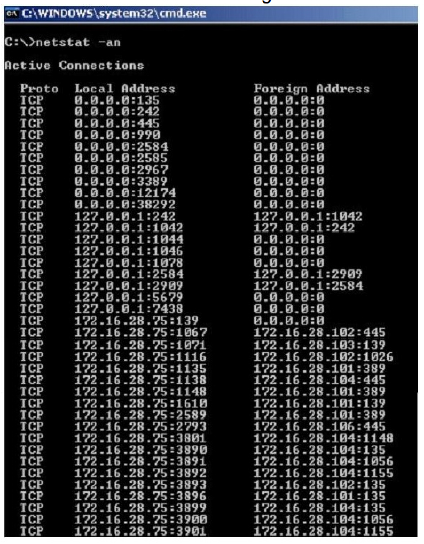
Jack Smith is a forensics investigator who works for Mason Computer Investigation Services. He is investigating a computer that was infected by Ramen Virus. He runs the netstat command on the machine to see its current connections. In the following screenshot, what do the 0.0.0.0 IP addresses signify?